Indicators on It Managed Service Provider Near Me You Need To Know

Functioning with a Managed Service Supplier like Custard implies your data will certainly be safe, whether that be from human error, flooding, fires, or something else., your service can profit from a substantial power conserving, which will in turn decrease your carbon footprint as well as lower prices to your service.
Managed IT services are a type of outsourcing in which an independent IT provider takes on the duty for the monitoring of an organisation's computer systems. This is typically carried out in exchange for a month-to-month cost and it's a method simple as well as efficient means for a company to obtain devoted IT competence without needing to work with or educate staff.

Offering companies with regular, cost-effective solutions such as cloud storage space, information cybersecurity, information loss prevention and also network surveillance. The MSP supplies remote IT support to organizations that would or else require to pay an IT division in-house. One of the most essential elements of MSPs is the emphasis they place on offering aggressive assistance.
The Best Guide To Managed It Provider
By outsourcing your IT solutions to IT experts, you can ensure that your computer system systems are always protected and you're never ever caught unsuspecting by an innovation failure. The future of taken care of solutions is all about handling the intricacy that includes all of the various other technologies that are being made use of and also the press in the direction of digital improvement; as the vast majority of companies are actively functioning in the direction of coming to be electronic initial services.
The very best way to scale a service is to automate. The development of managed IT services is an excellent instance of exactly how organizations are doing simply that. Managed IT solutions permit services to contract out the maintenance and also monitoring of their technology as well as eliminate the ineffectiveness related to an internal it team, that have ended up being all the more glaring in a pandemic economic climate - https://azlocallists.com/information-services/cx-it-services-melbourne-victoria/.
With COVID-19 creating unprecedented disturbances to standard functioning atmospheres all across the world, the currently indicates that taken care of solutions are much more. As a matter of fact, in their yearly record on the international Managed Services Market, Marketsand, Markets anticipated that the from USD 223. 0 billion in 2020 to a monstrous USD 329.
Some Known Details About Managed It Provider
The future of handled services has everything to do with transparency. Customers are requiring to know just how their money is being spent and also they desire to recognize what actions their vendors are taking to ensure their information and their businesses are risk-free with cybersecurity capacities progressively becoming an essential differentiator between an ordinary and also leading handled company.
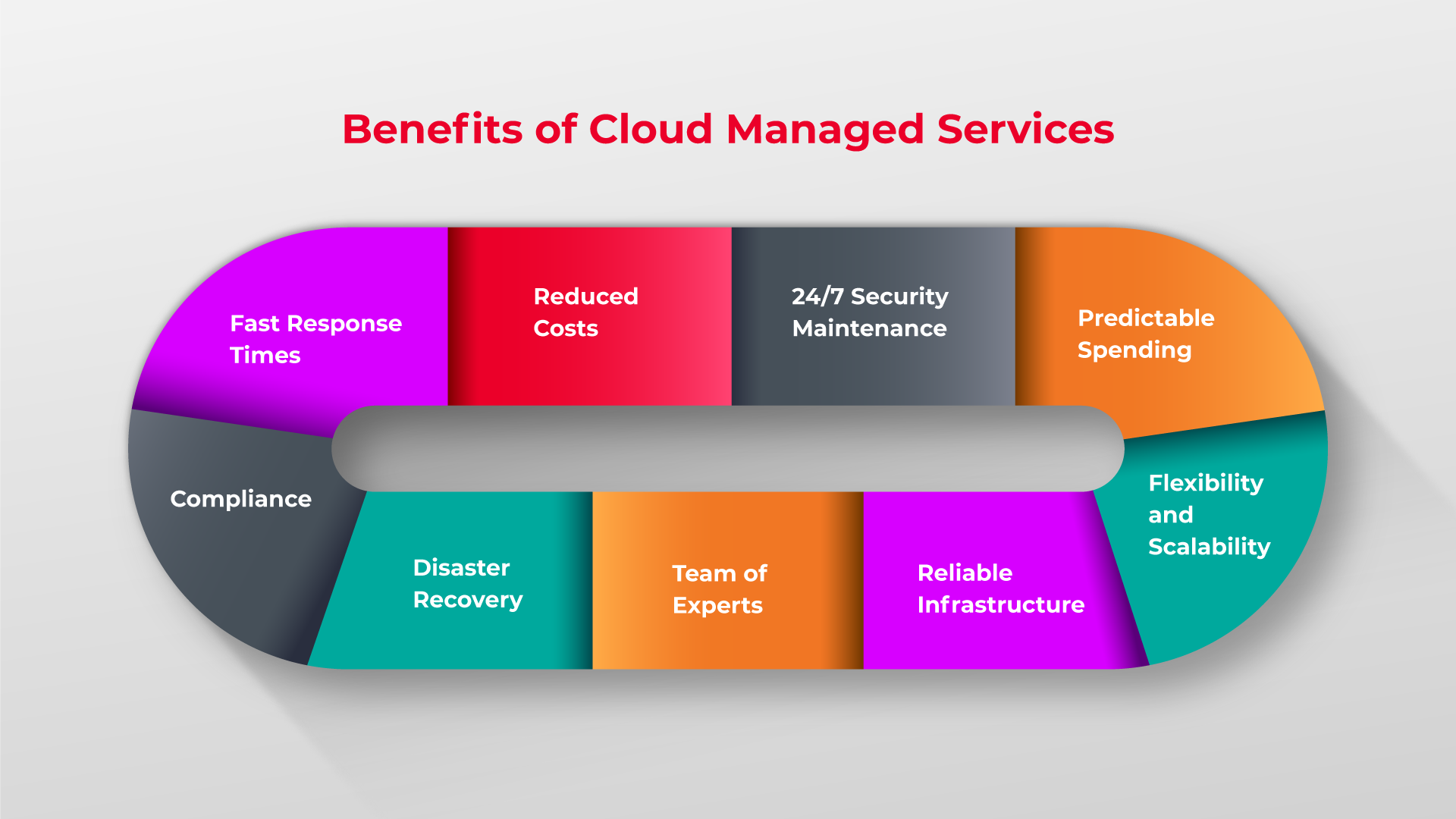
However, over time, it came to be clear that this design came with several shortages. The design fell short to adjust to the transforming nature of the IT industry. It concentrates on one-off solutions to issues, but doesn't address underlying troubles within the whole facilities as well as larger IT needs. This leaves companies susceptible to future failures and system failing.
As a matter of fact, Outsourcing a taken care of service carrier will certainly eliminate these problems, while giving many other advantages. One of the most innovative elements of handled IT solutions is the capacity to utilise an Online Principal Information Police officer (v, CIO)/ Online Chief Info Gatekeeper (v, CISO). These police officers work as a marked specialist, providing ad-hoc, round-the-clock IT sustain to your service. https://mexterbizlistings.com/information-services/cx-it-services-melbourne-victoria/.
Top Guidelines Of Cx It Services
For more information regarding contracting out a v, CIO/v, CISO, look into our what is a v, CIO post (managed IT support). So what are the advantages of click to read more handled IT solutions? A handled service company exceeds simply finishing one-off IT tasks. They are involved in all aspects of the network, safety, conformity, assistance, individual experience and carrying out brand-new modern technologies - https://nextgenbusinesscitations.com/information-services/cx-it-services-melbourne-victoria/.
These are some reasons using an MSP exercises to be very expense efficient: The average Australian wage of an internal IT personnel is $69,308. CX IT Services. Engaging a taken care of solution carrier sets you back a portion of this. Instead of investing on IT personnel salaries and needing to develop a full IT department, contracting out managed services implies that your firm is only using the people that are needed.
Rather than working with boosting modern technology performance as well as productivity, break/fix-it company gain from network downtime and also other IT problems. The first investment is usually reduced as you'll be paying for a functional expenditure as opposed to a capital investment. You will not have to invest in high in advance costs on software, equipment and various other IT resources.
Cx It Services Fundamentals Explained
No matter of the quantity of assistance your service needs, you'll just be paying a level fee for the service every month. When you make use of handled services, you're basically employing IT specialists with all the essential experience, credentials, and also training.
MSPs can make sure that all your systems are certified with the essential laws to prevent any type of danger in the future. This includes making certain that your business fulfills all PCI Safety And Security Specifications. PCI compliance consists of checking off items such as setting up and also keeping a firewall software, restricting accessibility to sensitive customer information as well as the routine screening of safety and security systems.

In addition, skilled support as well as training will certainly be conveniently available for users/employees/staff seeming more effective on the systems. An MSP will certainly have the ability to carry out a new technology roadmap that addresses both the temporary as well as long-lasting innovation objectives and purposes of your business. This offers businesses with invaluable guidance on what instructions your company need to move in the direction of.
The 7-Second Trick For Managed It Provider
That's why having 24/7 day-and-night support comes in extremely useful when utilizing a handled service company. MSPs sometimes also supply on-call alternatives and also weekend break support making them quickly obtainable in minutes of distress.